There can be a number of reasons why someone would need to hack Instagram password. These can include forgetting a password or having an account hacked with the details changed. We will detail the working methods so that you can gain access to an IG account. This guide will show how these methods work so that you can either apply them yourself or remain knowledgeable to guard yourself against them being used on your account. There is no prior knowledge required to follow these methods as they are fairly simple and easy to understand. Our guide is easy to follow and will show you all the best working methods to hack Instagram account in 2024. Some methods explained here are not that simple such as a single-app-usage methods (hacking performed with a help of pre-made specific hacking software) and may require multi layer of different techniques to do it successfully. However, you should carefully read our disclaimer below. It is important that you properly understand our disclaimer which is crucial to keep our guide to stay for long term and accept educational-purpose of its nature.
Note: Credits for gathering some of the methods here goes to GeekSpeakr’s study.
– Table of Methods:
1. Instagram Password Cracker “IGHacko”
2. Phishing
3. Keyloggers
4. Social Engineering
5. Use of Email & (or) Phone Number
6. How to Protect Your Instagram Account From Getting Hacked
Instagram Password Cracker “IGHacko”
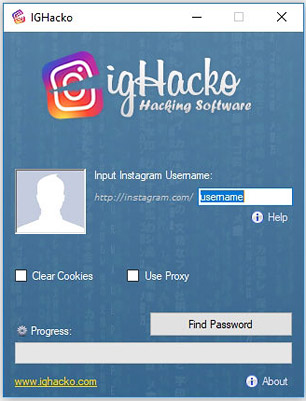 This software provides an effective option for hacking Instagram passwords. This tool utilizes the classic “brute-force” method of hacking into an account. It is a simple to use application that can get you right password within minutes. The effectiveness of this tool depends on how strong the password of the user is. It uses a customized version of brute force that is tailored towards of hacking IG. It bypasses Instagram’s own protection mechanisms which usually limit the number of login attempts allowed. It does through a built-in VPN which allows the brute-force method to exploit the password. IG Hacko tool works on MacOS, Windows, Android & iOS devices.
This software provides an effective option for hacking Instagram passwords. This tool utilizes the classic “brute-force” method of hacking into an account. It is a simple to use application that can get you right password within minutes. The effectiveness of this tool depends on how strong the password of the user is. It uses a customized version of brute force that is tailored towards of hacking IG. It bypasses Instagram’s own protection mechanisms which usually limit the number of login attempts allowed. It does through a built-in VPN which allows the brute-force method to exploit the password. IG Hacko tool works on MacOS, Windows, Android & iOS devices.
You can download the IGHacko app from its official website (www.ighacko.com). This app is essentially an upgraded algorithm that has been specifically designed to target Instagram accounts. It is easy to use, even for novice users. Once the program has been started it automatically begins the algorithm will attempt to crack the password of the Instagram account. It works by exploiting inherent vulnerabilities that are present within Insta passwords.
Phishing
Phishing is a common method of password hacking and of the oldest cracking methods ever. It is a popular method due to its relative ease and effectiveness. Phishing involves creating a ‘fake’ login page that a user recognizes as an official Instagram page. The user then adds in their details into this page, and these can then be read by whoever owns the page. There are a number of ways that Instagram phishing strategies can be used to hack an account. One way is through email where the user will receive an email seemingly from IG asking to ‘change their password.’ This email may look identical to ones normally received from Instagram. Most users could not tell the difference upon first glance. Another way that phishing is used is by creating fake third-party applications that say a user may gain followers or help to manage their Instagram. This works in the same way as a user will enter their details on this page, and it will go into the hands of the hackers. It is difficult even to tell if you’ve been hacked using this method as the page will then redirect to the official Instagram website.
How to Make Instagram Phishing Page?
In this step by step guide, we will explain how you can make your own Instagram Phishing Page. This can be the perfect way to retrieve your account from a hacker.
- Download Files
The first step is to download a file which is known as “Index.htm.” We have a link to this file here. You then to download the file which is known as “Hack.php.” The link to this file is here.
- Create a Web-Hosting Account
The second step is to create a web hosting account. This will be required for the website to host your phishing page on. There are numerous paid and free options available for hosting. X10hosting.com or 000webhost.com.
- Add the Files to Your Web-Hosting Server
Once you have a web-hosting account ready to go, the next step is to add the downloaded files onto the server. You should go the “manage website” section which will be visible after you have logged in to your web hosting server. You will then see an option to “upload website” which will open up a file manager. This will allow you to drag and drop the files onto the web hosting server. In the file manager, you will see a directory titled “public_html.” You should open this directory and upload both of the files into it. You will know that the files have been uploaded successfully if you see them both appear in the directory.
- Test your Phishing Page
The final step involves testing that your phishing page is working properly. You should stay in the directory and right click the file on the “index.htm” file and click on view. This will open up your phishing Instagram page. Your web browser will show the exact URL of this page. You should copy this and keep it as the target page. This is the link you must send if you want to hack someone’s Instagram account. You can see any passwords that may have been entered by going on your URL and adding, “/password.html” at the end of it. This will show the passwords that have been entered on your page.
Luring your Target to the Phishing Page
Once your page is set up and ready to go, the next step will be attempting to lure your target to click on the page and enter their details. There are a number of ways that you can go about this. One way to get them to click the link is by pretending to be an IG influencer. You can DM them the link directly from Instagram and claim that the link is for an app for a partnership or to help them gain more followers. Alternatively, you can claim that you are offering them a social media management tool that will help them use Instagram better.
Depending on your target, you can also text or email them the link. It is important to tailor your approach based on what the person is most likely to think is real. The aim is to get them to click on your phishing page and enter their details. Once they have entered their details, you will immediately receive their username and password and have access to the account. They will not know they were hacked, as the phishing page will simply redirect to the actual Instagram application or website. Phishing is directly related to social engineering, and we will discuss the specifics of social engineering later on in the article.
Keyloggers
 Keyloggers are another method of hacking. A keylogger is an application that records the exact keystrokes of a user. This means that when they type their username and password, it will be visible to the person who is running the keylogger application. You can use keyloggers for both PCs and Smartphones. We have a list of the most effective and easy to use keyloggers.
Keyloggers are another method of hacking. A keylogger is an application that records the exact keystrokes of a user. This means that when they type their username and password, it will be visible to the person who is running the keylogger application. You can use keyloggers for both PCs and Smartphones. We have a list of the most effective and easy to use keyloggers.
The best keylogger for Android/iPhone is ikeymonitor. It is easy to use and install on both devices. Once this application has been installed, it tracks every word that is typed which makes it easy to hack an Instagram account. There is also a free trial available for this keylogger. Another good keylogger application for iPhone devices is mSpy. It can be used on both jailbroken and non-jailbroken iPhones. The application runs silently once installed and is basically impossible to detect from the user. This gives you extra assurance that you can hack their “Insta” account without them finding out. One of the best keyloggers for Android is Spyzie. It is very easy to use and offers complete monitoring, whilst remaining hidden in the user’s phone.
Additionally, you can use keyloggers on Windows devices. These can be used if the targeted person is logging onto Instagram using their laptop or PC. One of the best keyloggers for both Windows and Mac OS devices is Kidloggers. It is by far the best free keylogger as it includes all the essential features needed to hack into someone’s IG profile. Another good keylogger for Windows is Revealer Keylogger. The additional benefit of this keylogger is that it allows you to adjust startup settings and it remains undetectable. It is easy to use any of these keyloggers to obtain the username and password when the person types it in. The exact keystrokes are recorded privately and sent directly to you. This will provide you access into the Instagram account.
All keyloggers will have easy to use databases that contain everything a person has typed with the program installed. This will include the username and password. You can simply copy and paste these credentials and enter them into the Instagram log-in page. The best part of keyloggers is that they are virtually untraceable. They run on the user’s device without the user ever being aware. Once, you have the password you can easily uninstall the keyloggers without being detected. They can be turned off remotely, which means the user will not have an idea of who accessed their account. The keyloggers we have listed are all very effective for their devices. However, they have some differences which you should check for yourself. Some are paid, others offer free trials, and the rest are completely free to use. The best keylogger for you will depend on the device you are using and how the installation of the program will be conducted. These applications offer more than just keystrokes which can be useful in obtaining other information if it is required. If for example, a hacker also had access to your email address, a keylogger can take the details of both the email account and Instagram account. This can help restore your account back to how it was and prevent any hacker from changing the password through using the email.
Social Engineering
 Social Engineering is a method that isn’t reliant on a specific technology to break a password. It is reliant upon the human factor. It has become an increasingly popular way to target users directly in order to hack their Instagram accounts. The most simple type of social engineering is merely trying to guess the password. This is easier if you know the person. Most people will have their passwords set to something common such as their birthday, name of their dog, or the name of their girlfriend. Individuals can gather these details in normal conversation, and the other person would not be aware of the true intentions. The first step of social engineering is simply trying to guess the password. However, there are more advanced steps that feature manipulation in order to retrieve the password to an account. The concept of phishing which we already discussed above also involves social engineering as the person must be fooled into clicking a link that takes them to the phishing page. You can only use social engineering to hack a password after you have planned your strategy. This should involve a focused approach so that you know which steps you will take. It can begin by becoming familiar with your target. It should then progress to getting the target to admit some clues about their password or even accidentally mention their password.
Social Engineering is a method that isn’t reliant on a specific technology to break a password. It is reliant upon the human factor. It has become an increasingly popular way to target users directly in order to hack their Instagram accounts. The most simple type of social engineering is merely trying to guess the password. This is easier if you know the person. Most people will have their passwords set to something common such as their birthday, name of their dog, or the name of their girlfriend. Individuals can gather these details in normal conversation, and the other person would not be aware of the true intentions. The first step of social engineering is simply trying to guess the password. However, there are more advanced steps that feature manipulation in order to retrieve the password to an account. The concept of phishing which we already discussed above also involves social engineering as the person must be fooled into clicking a link that takes them to the phishing page. You can only use social engineering to hack a password after you have planned your strategy. This should involve a focused approach so that you know which steps you will take. It can begin by becoming familiar with your target. It should then progress to getting the target to admit some clues about their password or even accidentally mention their password.
Social engineering can also be done through phone calls or emails. A person may fake their credentials and ask that the password of the user be given up. They may pretend to be an employee of Instagram. Social engineering works by gaining the trust of your target and slowly pressuring them into giving up their password. It cannot work on everybody but is especially effective at those who are relatively gullible and prone to follow orders in real life. Most people can be fooled with enough manipulation and eventually can be willing to give up their passwords. Social engineering is all about closely understanding human behaviour and manipulating it to get what you want. In this case, the thing that you want will be an Instagram password. You can use social engineering by creating false emails and by impersonating someone else on the phone. It takes real skill and nuance; however, when applied correctly it can be one of the most effective strategies to hack Instagram passwords.
Use of Email & (or) Phone Number
In the video clip below you can learn how to access an Instagram account if you know an e-mail address used for signing up for an IG account, or a phone number which is attached inside its security settings for easier recovery.
This is how you can do it:
How to Protect Your Instagram Account From Getting Hacked
 There are a number of measures that you can take to protect your Instagram account from being hacked or being used by unauthorized persons. If you follow these simple steps, then you can have the reassurance that your Instagram account will remain protected. Some of these steps may seem like obvious or common knowledge. However, even the smartest people occasionally make lapses that can make their account vulnerable to being hacked. None of these protection tips are difficult to implement, but they do require you to pay close attention to your account and to always remain alert of any suspicious activity.
There are a number of measures that you can take to protect your Instagram account from being hacked or being used by unauthorized persons. If you follow these simple steps, then you can have the reassurance that your Instagram account will remain protected. Some of these steps may seem like obvious or common knowledge. However, even the smartest people occasionally make lapses that can make their account vulnerable to being hacked. None of these protection tips are difficult to implement, but they do require you to pay close attention to your account and to always remain alert of any suspicious activity.
- Pick a Strong Password
The most important tip for preventing your “Gram” account from being hacked is picking a strong password. This stops someone from guessing your password, and it also provides security against brute-force attacks. You also shouldn’t use the same password as you do for another account. Data breaches are common, and hackers often try the same passwords for multiple accounts. It is important to use a separate password for every account that you have online. We suggest a minimum of 10 characters for your password. This is above the official recommendation, but this length provides better protection. It should not be something that can be commonly guessed such as your name or the name of any pets that you have. It should contain at least one capital letter and at least one special symbol. The inclusion of these can make it near impossible for someone to hack your account. It is also important to update your password on a yearly basis.
- Turn on Two-Factor Authentication
Instagram already has a very good feature that protects against hacking attempts, yet many users remain unaware of it. There is a two-factor authentication available to all users. It provides a high level of protection to your account. It essentially means that only recognized devices can access your account. If a login is detected from a new device, then a text code must be entered. This would come on your phone, and therefore a hacker would be thwarted as they could only have this code if they also had your phone. This also makes it difficult for hackers to change any settings as any changes would also require a text code confirmation.
- Secure your Email Address
It isn’t just your Instagram account that should be kept secure. Your email address opens up a backdoor entrance to access to your Instagram account. It also holds the keys for your other accounts on the internet. A hacker with access to your email has potential access to a lot of sensitive information. They can go through the process of ‘forgot your password’ on Instagram and start changing the details of your account. This can make it impossible to retrieve a hacked account. You need to take the same safety precautions towards your email address. This includes setting a strong password and considering enabling two-factor authentication.
- Remove Access to Third Party Apps
Instagram recently experienced controversy due to suspicious third-party applications hacking into user accounts and making changes without their permission. You can manage the use of third-party applications from your profile. You can click on ‘settings’ and then click on ‘authorized apps.’ This will present a full list of applications that have access to your account. Any applications that you don’t recognize you should revoke access to. You should regularly check this page of your profile to ensure that unwanted applications haven’t somehow accessed your Instagram profile.
- General Tips
There are also some general tips that you should be aware of. These are mainly common sense, but it is important to remember these precautions. The first thing to keep in mind is to always log out of Instagram when you are using a public computer. This prevents anyone else from accessing your account. You should also uncheck the ‘remember me’ box. Another obvious tip is never to share your password with anyone. You shouldn’t even share any hints, not even to people you trust. Social engineering can lead to you trusting people who have malicious intents. The only person who knows your password should be you. You also rvery wary of any text messages or emails you receive. You should never click on any links from email sources that you do not recognize. These can be links to phishing pages which can steal your password and hack into your account.
Conclusion
You will now have a better understanding of the latest methods of hacking Instagram passwords. All of these methods are working well at this moment, and it just depends on how well you can apply them. The method that works best for you will depend on your situation. These methods will allow you to gain access to an account that you may have forgotten the password to or an account that was previously hacked. They will allow you to take back control of the account even if it has been changed. By understanding these methods, you can also take measures to prevent anyone gaining unauthorized access to your account. There are many ways for someone to gain access, but following the steps above will keep your account safe and secure.
DISCLAIMER:
All information listed in this article is for informational purposes only. The methods mentioned here should ONLY be used to gain access to your own account. This may be an account that has been hacked or one that you have been locked out of. Under no circumstances should you use the methods listed in this guide for any illegal purposes. We are not promoting or suggesting that anyone should hack someone else’s account. Please be sure to follow the community guidelines set forth by Instagram which can be found here.
